Identifying Malicious DNS Tunnel Tools from DoH Traffic Using Hierarchical Machine Learning Classification | SpringerLink

Identifying Malicious DNS Tunnel Tools from DoH Traffic Using Hierarchical Machine Learning Classification | SpringerLink
DNS Tunneling Simulation Topology 3.1. Log aggregation and simulation.... | Download Scientific Diagram









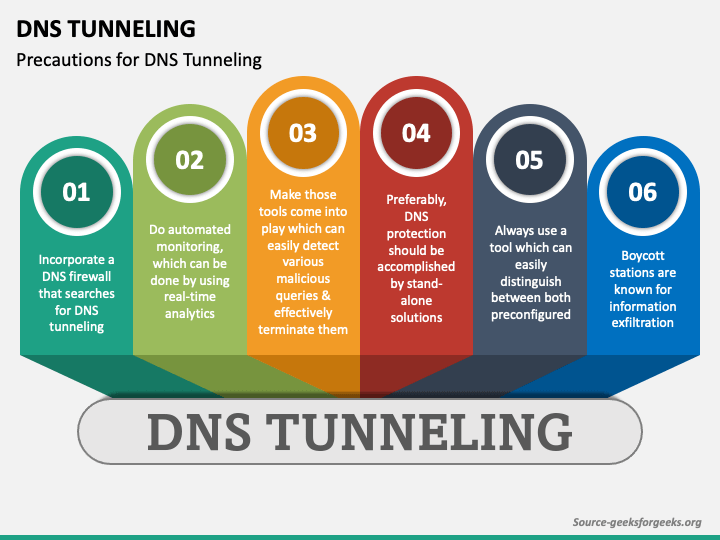
![PDF] Performance assessment and analysis of DNS tunneling tools | Semantic Scholar PDF] Performance assessment and analysis of DNS tunneling tools | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7f3bc9a13f911b1e2d1d981fc5c83c5fcf62d2fd/6-Figure2-1.png)